Authorization: Tenant and Role Mapping Examples
Overview
Remote Auth requires assignment of roles and tenants for every user login via the authorization mapping rules. Authorization is assessed on every login and the user record is updated. Upon successful user login via an external authentication server, all mapping rules are evaluated; tenant and role pairs are added to user access list.
NSX Advanced Load Balancer supports user profile mapping for remote users.
Configuring Remote Authentication
By default, a Controller has only local authentication established.
To configure remote authentication using the NSX Advanced Load Balancer UI,
-
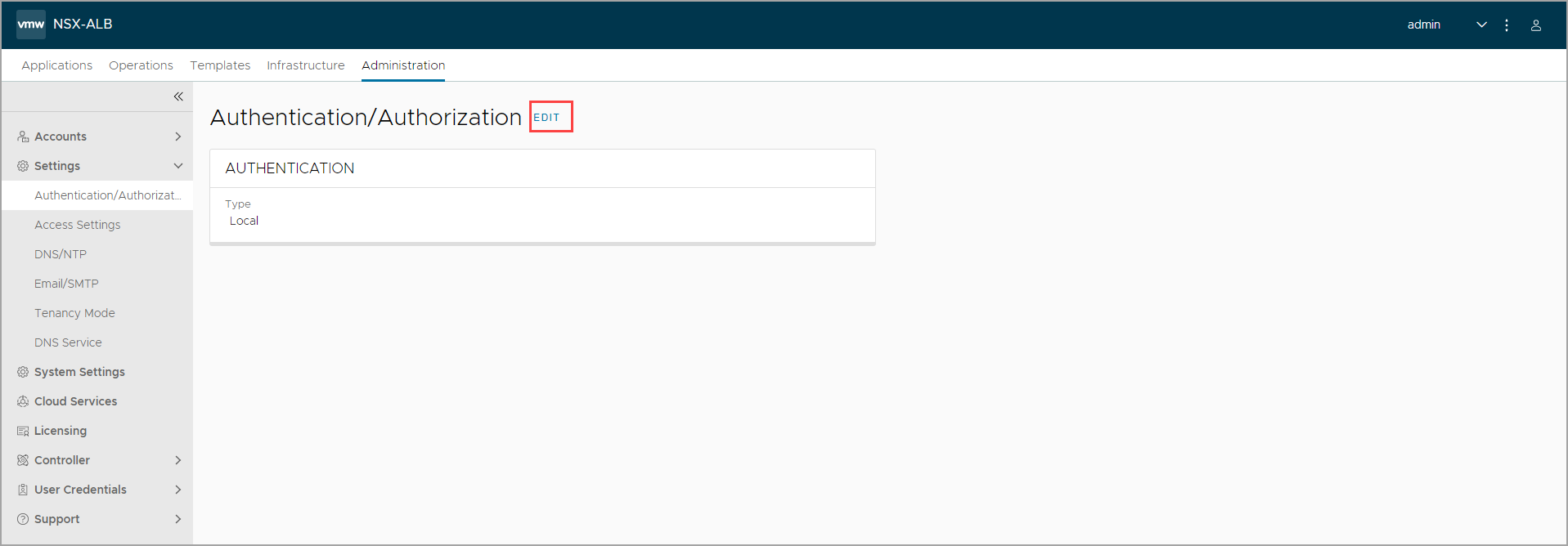
Navigate to Administration > Settings > Authentication/Authorization.
-
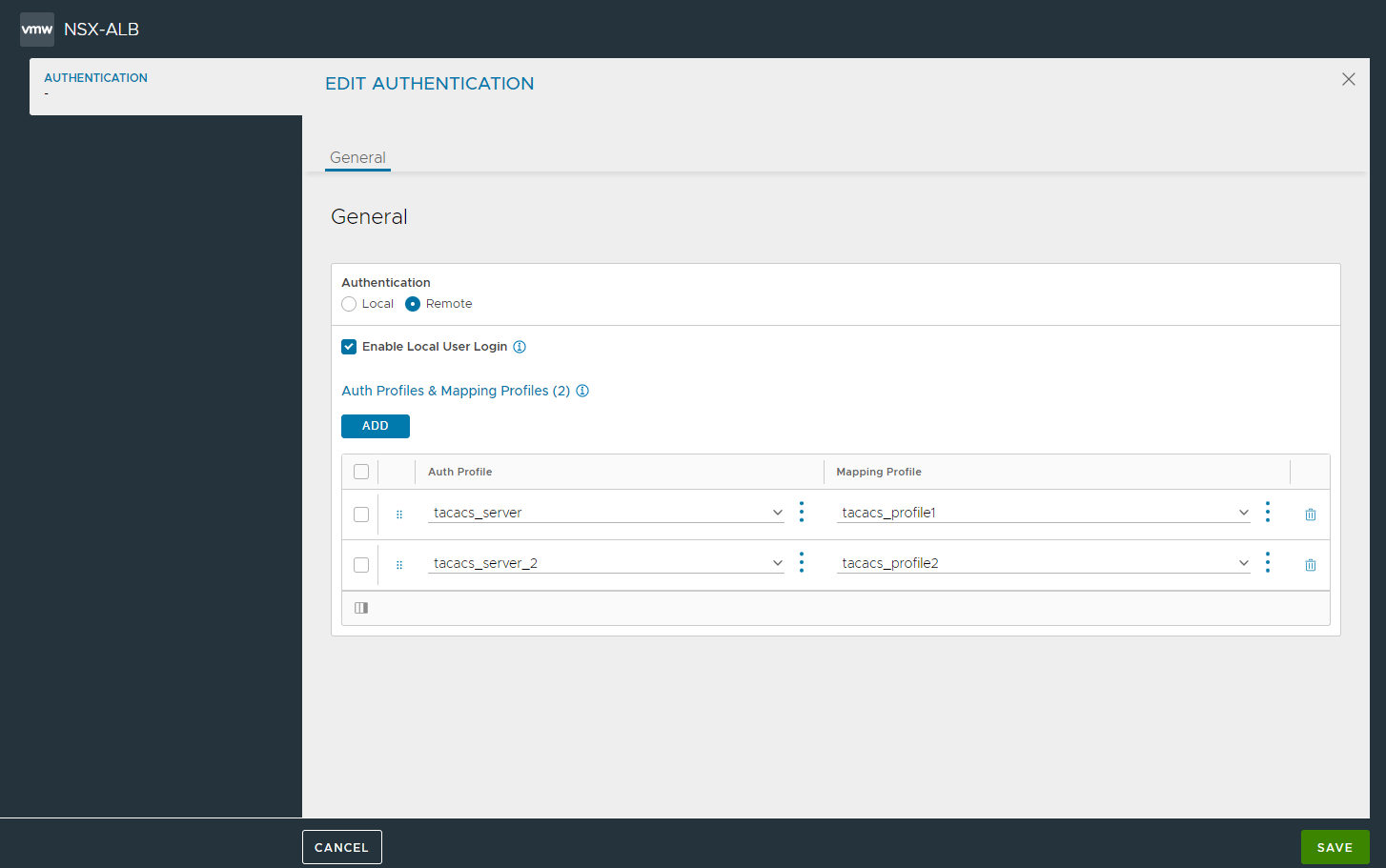
In the Edit Authentication screen, select Remote as the Authentication method.
-
Select Enable Local User Login to allow users from the local user database to log in with their user credentials.
-
Under Auth Profiles & Mapping Profiles, click Add.
-
From the Select Auth Profile select an existing remote auth profile or click the vertical menu icon (three dots) to create a new auth profile.
-
Click Save.
Note Tenant and role mapping are available only with remote authentication.
Multiple remote authentication profiles can be configured using the NSX Advanced Load Balancer UI under the following conditions:
- Any number of auth profiles (more than 2) can be created provided they are of the same type. Consider the following examples to understand this further:
Profile Types Result Reason - TACACS
- TACACS
- TACACS
Successful All profiles are of the same type - TACACS
- TACACS
- LDAP
Fails with an error All the profiles are not of the same type - If there are only two auth profiles configured
- The primary auth profile has to be SAML auth profile.
- Both profiles cannot be SAMl. So if SAML is the first auth profile, then the second profile has to be any profile other than SAML
Consider the following examples to understand this further:
| Primary Auth Profile | Secondary Auth Profile | Result | Reason |
|---|---|---|---|
| SAML | LDAP | Successful | The primary and the secondary profiles are of different types |
| SAML | SAML | Fails with an error | The primary and secondary profiles are both of type SAML |
| LDAP | TACACS | Fails with an error | The primary auth profile is not of type SAML |
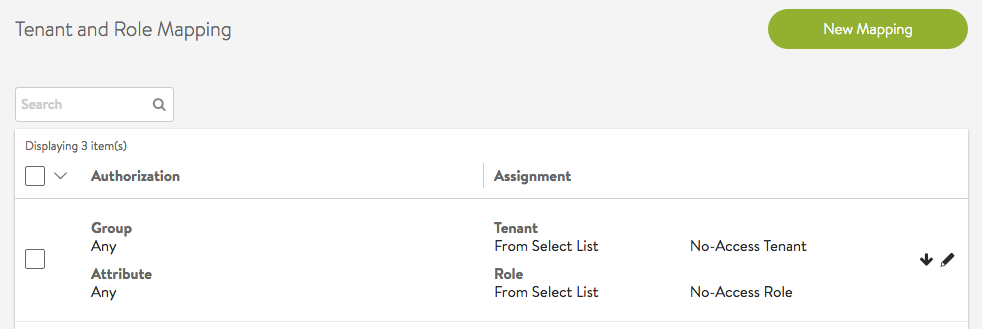
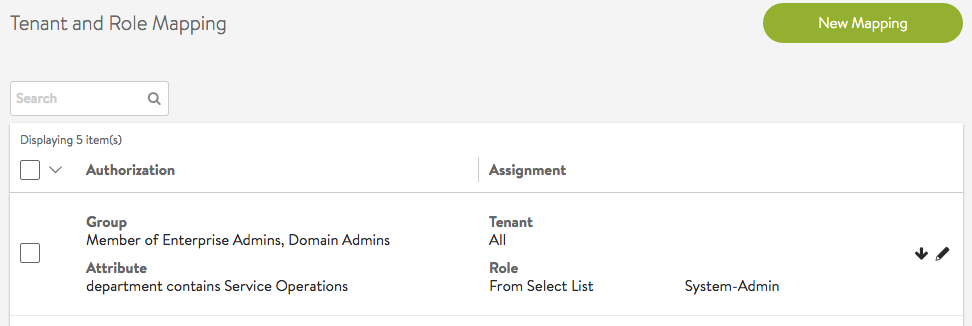
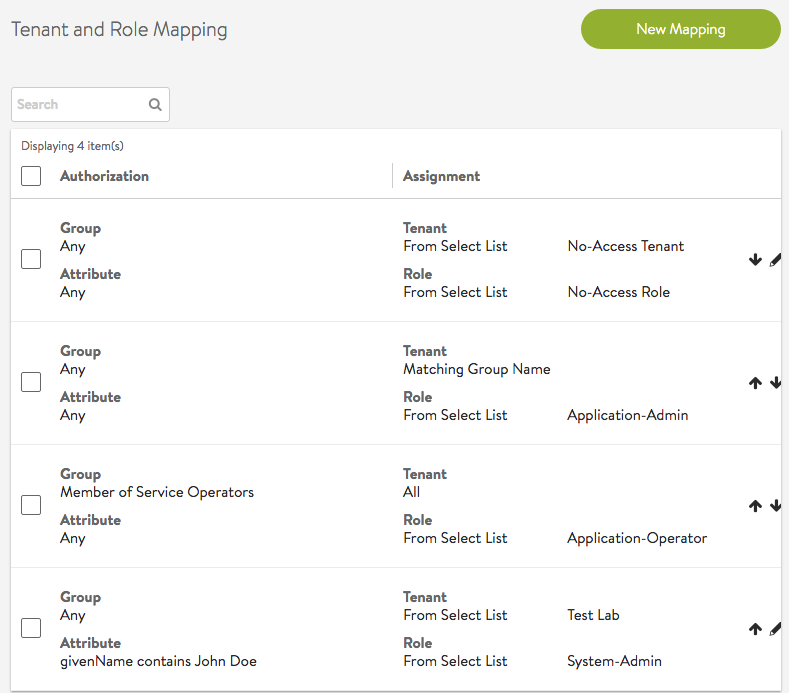
Any Group/Any Attribute Rule
A rule with any group or any attribute applies to all users and can be used as a default option. The rule below assigns every user to a least privileged role and tenant (Note, the role and tenant need to configured to only allow least privileges). If the user is not assigned any more role/tenant pairs, the least privileged access will take effect after login.
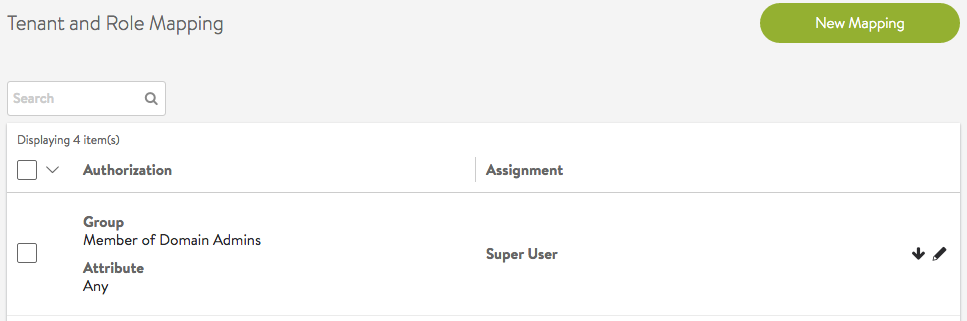
Super User Rule
A rule can be configured to assign Super User privileges to a user. This user will have access to all tenants with the most privileged role. Once a user is super user, no other tenant/role mapping assignments will make a difference to the user’s access.
Attribute and Group Match
A mapping rule can be required to match both an attribute and group requirement. This will ensure a more specific assignment of role(s) and tenant(s).
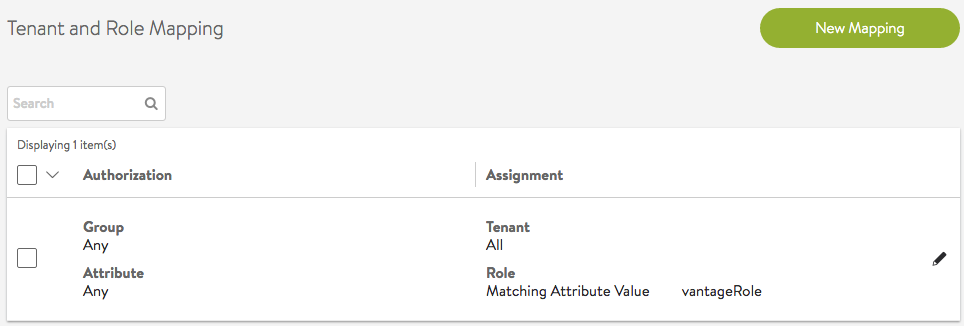
Assign Matching Attribute Values
LDAP/TACACS+ attribute “vantageRole” for a user can have one or more values. For each value, if there is a configured role with the same name, the role is assigned to the user with access to all tenants. A user session can end up with multiple roles and the most privileged role will take effect.
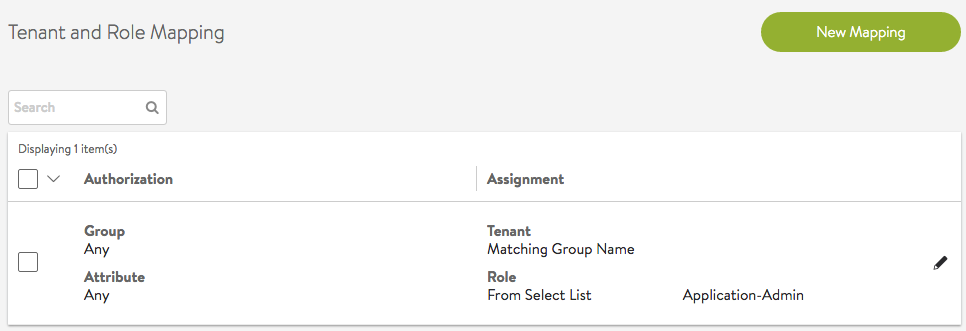
Assign Matching Group Names
A user can be a member of multiple LDAP/AD groups. For each group, if there is a configured tenant, the user will be given access to the tenant, along with any other tenants the user may already have obtained access via matching rules.
Configuring Default Tenant for Remote Users
When configuring auth mapping rules, you can now select default tenants. When a remote user is created, the tenant selected here will be used as the default tenant.
- From the NSX Advanced Load Balancer UI, navigate to Administration > Authentication/ Authorization. Click New Mapping or edit an existing auth mapping rule.
- Under Action, select Custom Mapping.
- Click Add.
- From the User Tenant dropdown list, click Selected.
- Select the required Tenants.
Note: If multiple tenants are created in the mapping rules, the first tenant selected is taken as the default tenant by default.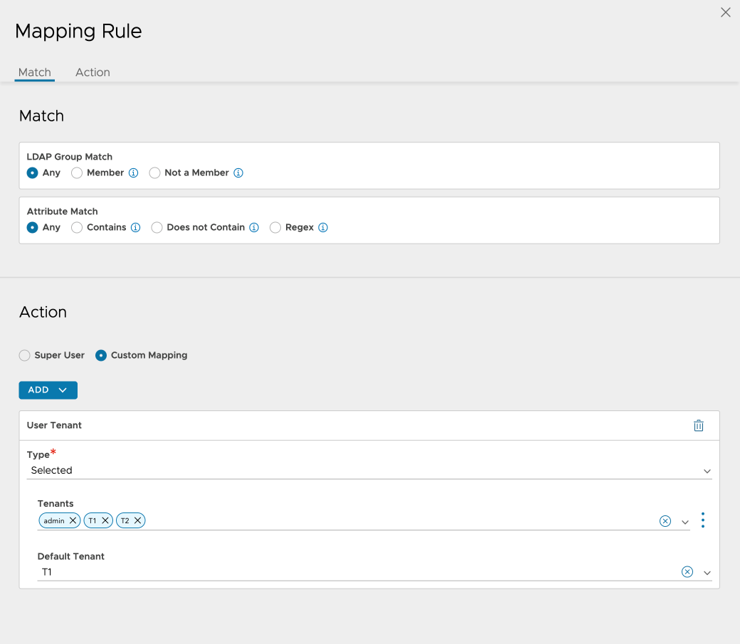
- Click Save.
Alternatively, default tenant for remote users can be configured using the field default_tenant_ref through the CLI as shown below:
[admin:10-102-64-241]: authmappingprofile:mapping_rules> default_tenant_ref admin
[admin:10-102-64-241]: authmappingprofile:mapping_rules> save
[admin:10-102-64-241]: authmappingprofile> save
+----------------------+---------------------------------------------------------+
| Field | Value |
+----------------------+---------------------------------------------------------+
| uuid | authmappingprofile-46400ba5-9f05-4ec9-9464-e188010ce7b7 |
| name | saml |
| type | AUTH_PROFILE_SAML |
| mapping_rules[1] | |
| index | 0 |
| is_superuser | True |
| default_tenant_ref | admin |
| tenant_ref | admin |
+----------------------+---------------------------------------------------------+
[admin:10-102-64-241]: >
Default tenant mapping based on the tenant selected, is as shown below:
| User Tenant | Behavior | Default Tenant | Description |
|---|---|---|---|
| All | Admin | All tenant values | Any user-specified tenant is used. In the absence of user-defined tenants, admin will be selected as the default tenant |
| Admin | Admin | All tenant values | Any user-specified tenant is used. In the absence of user-defined tenants, admin will be selected as the default tenant |
| Selected | Tenant ref | Only selected tenant values | Any User-specified Tenant that is part of selected tenant list otherwise Must check will throw an error while creating a new mapping For example, if the selected tenant list has T1 and T2 but the user has provided T3 as default tenant then must check will throw an error "Default tenant is not in selected tenants list. If the user has not selected any tenant but has provided default tenant ref then the error **Please add at least one tenant in the selected list** is displayed. |
| Attribute Regex | Tenant ref | All tenant values | User-specified tenant |
| Attribute value | Tenant ref | All tenant values | User-specified tenant |
| Group name | Tenant ref | All tenant values | User-specified tenant |
Note:In case of Attribute Regex, Attribute value, Group Name, if the user has entered a tenant that is not part of the user tenant list (retrieved at runtime on the basis of Attribute Regex, Attribute Value, Group Name, Group Regex match), then the first entry in the retrieved list will be assigned as default tenant from the tenant list. For example, U1 can be assigned T1, T2 but T3 is provided as the default tenant at that time either T1 or T2 will become the default tenant based on which one is first entry in the retrieved tenant list.
Examples
Multiple Groups Mapping to Different Roles
This example illustrates the case of an IT team with three user groups — super-admins, app-admins, operations — where the following applies:
- Super Admins: may access all tenants, all settings, hence, they are super users.
- Application Admins:
- may only create, read, update and delete virtual services and other profiles.
- may not create clouds.
- Application Operators: have read-only access.
Separate mapping rules are required to map users from each group to different role/tenant assignments.
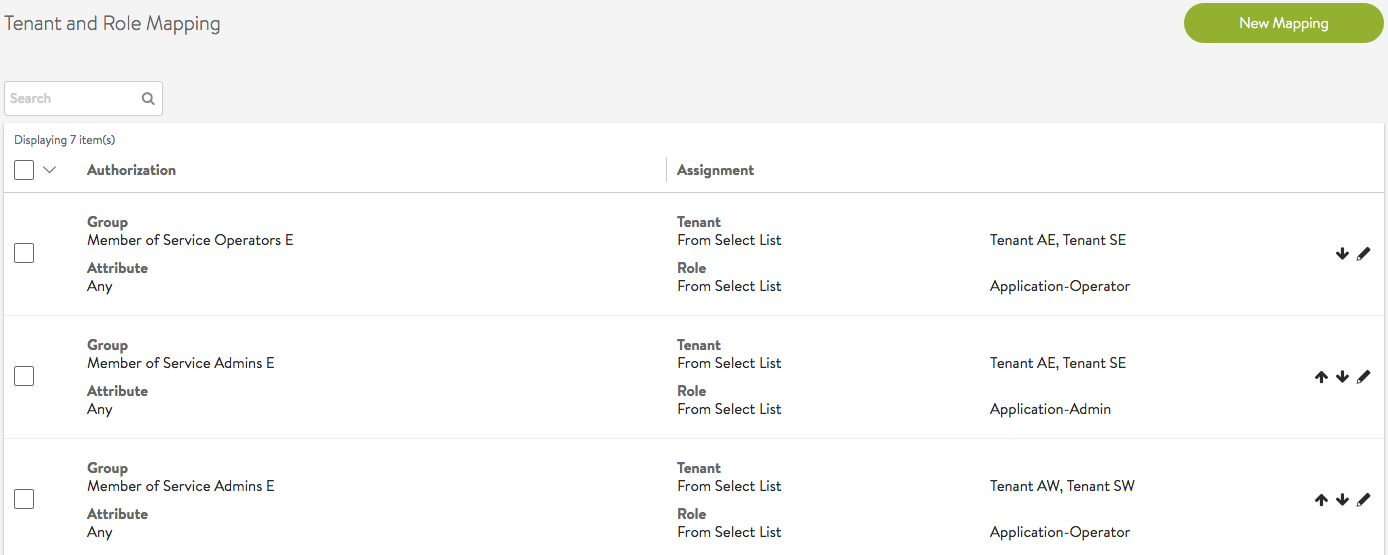
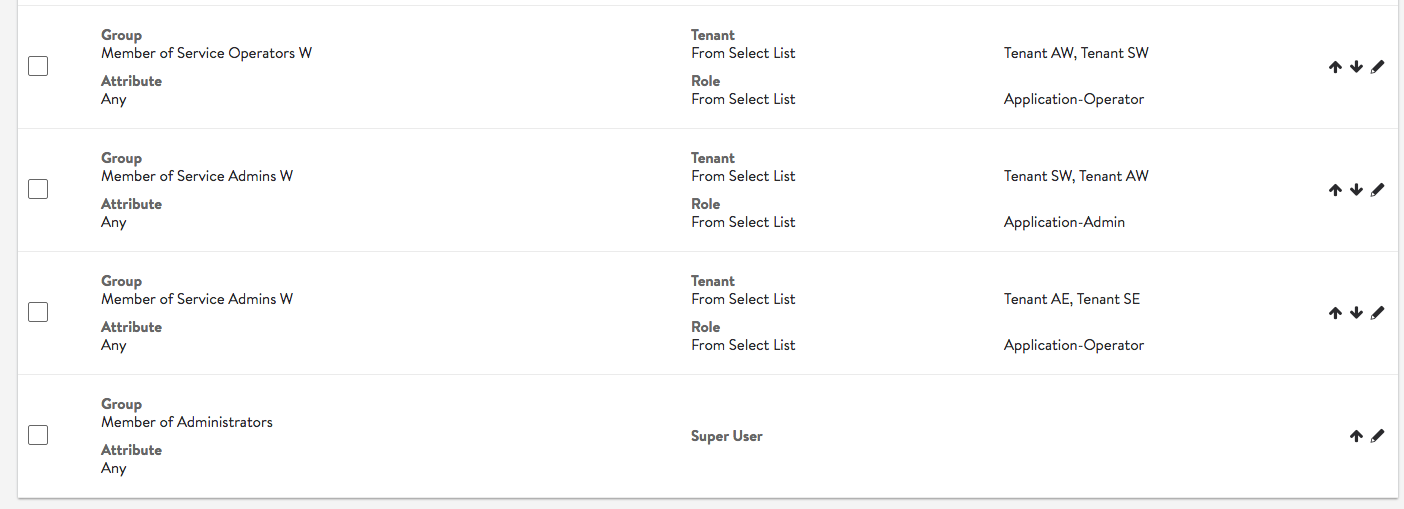
Multiple Groups Mapping to Different Tenants
This example illustrates settings for an IT team that expects tenant isolation except for a few super users.
- Super Admins: can access all tenants, all settings, hence, they are super users.
- Tenant Application Admins: have access to a few tenants — app owner for few tenants
- Tenant Application Operators: have access to a few tenants — cannot modify anything
- Tenant Application Admins/Operators: have access to a few tenants as app owners and other tenants as app operator folks.
In this example, members of group “Service Admins E” have read/write access (Application-Admin role) in tenants Tenant AE and Tenant SE, while they have read only access (Application-Operator role) in a few other tenants. “Service Operators” have only read-only access in their respective tenants.
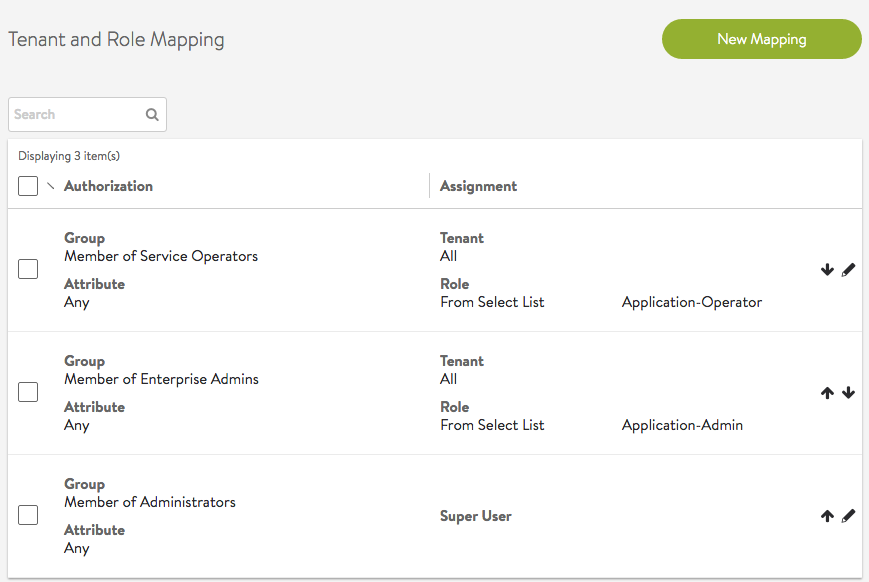
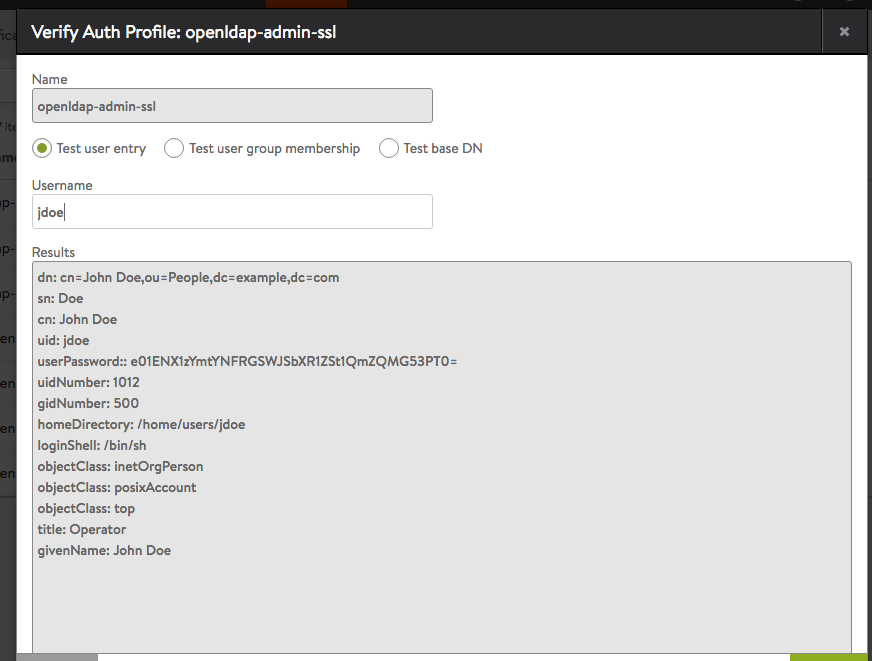
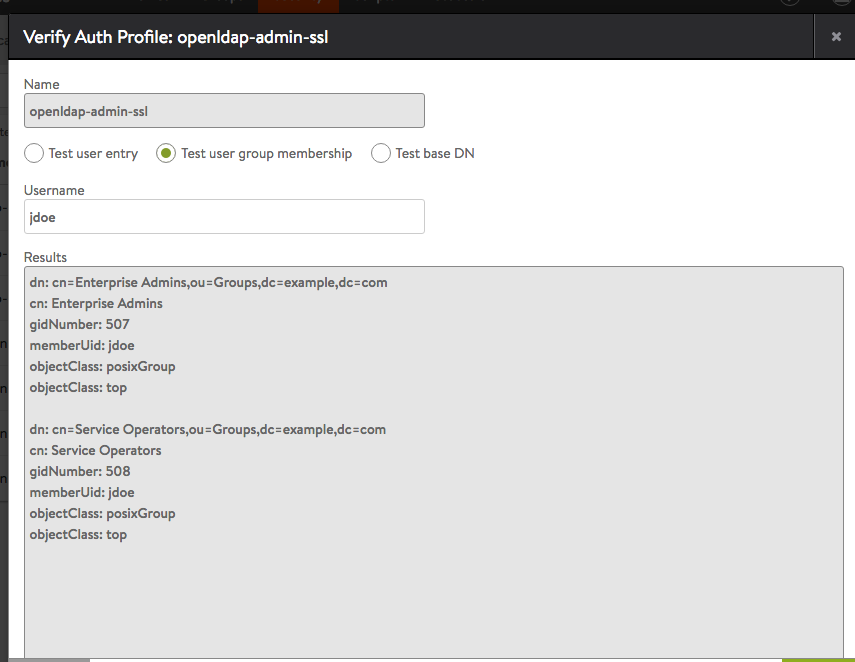
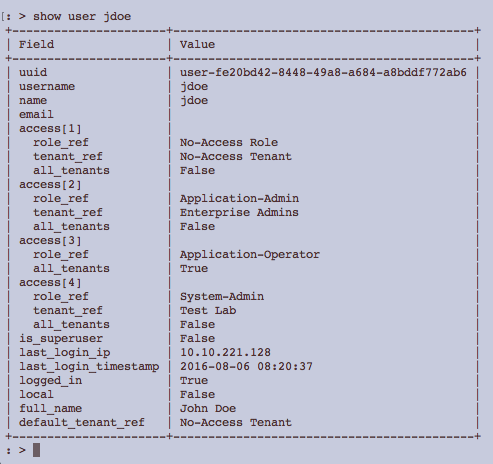
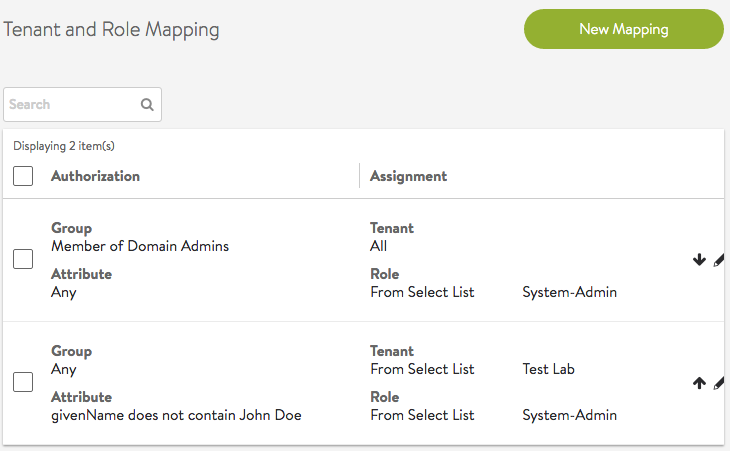
Multiple Authorizations for a Single User
In this example, login of user John Doe results in the user gaining access via multiple authorization mapping rules.
Multiple mapping rules are configured based on various group and attribute criteria.
The LDAP server is configured with user John Doe.
The LDAP server is configured with John Doe as a member of the groups Enterprise Admins and Service Operators.
After user John Doe logs in and all authorization rules are applied on the user session. Multiple role/tenant combinations are used to determine user privileges during user login. The user record shows the user successfully matched all 4 rules and role/tenant pairs were appropriately applied.
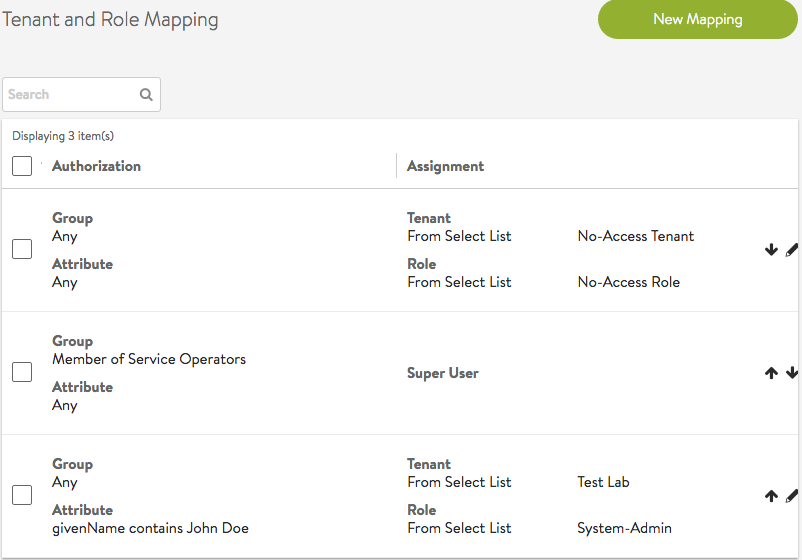
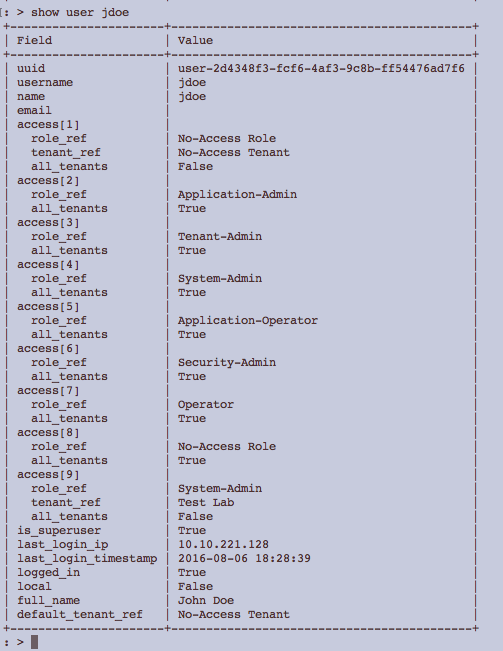
Multiple Authorizations Resulting in a Super User
In this example, login of user John Doe results in the user becoming super user.
Mapping rules make a member of the group Service Operators a super user.
Due to the super user access, user John Doe gets access to all tenants with every role.
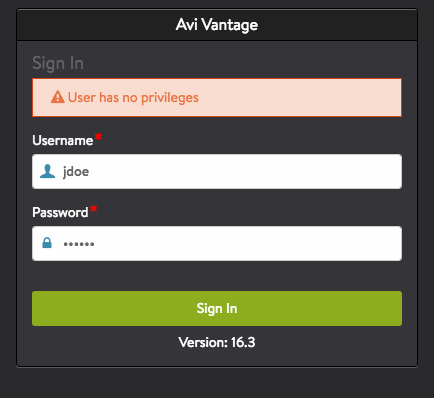
No Authorizations for a Single User
In this example, login of user John Doe results in the user not getting any roles or tenants.
Mapping rules are updated to keep user John Doe from having any privileges.
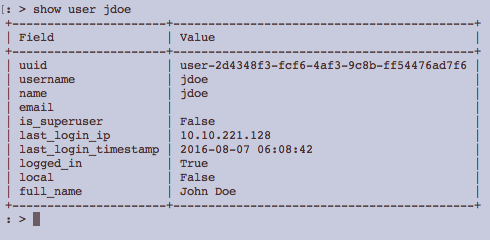
When user John Doe logs in, the user interface reports no privileges to login.
User record does not have any access entries.
Tenant to Role Mappings
Avi Vantage supports dynamically assigning tenant and role name based on a regex match. This requires a tenant or role variable to be configured in the regex to assign tenant/role name based on the regex. The variables must be in the (?P{tenant}regex) form
Example:
LDAP DATA
user: test_user
test_user is a member of the following groups:
-
lb_ap1234_test
-
lb_ap7890_test
Mapping Rule Configuration:
The following is the CLI format:
"attribute_match": {
"values": [ "lb_?P{tenant}\\w*)_test" ],
"name": "tenant",
"criteria": "AUTH_MATCH_REGEX"
}
"assign_tenant": "ASSIGN_MATCHING_ATTRIBUTE_REGEX",
"assign_role": "ASSIGN_FROM_SELECT_LIST"
"role_refs": ["https://10.10.24.204/api/role/[Role-UUID]" ],
}Result:
With this rule mapping and LDAP configuration, test_user will get ap1234 and ap7890.
You can configure the above rule in the CLI as follows:
configure authmappingprofile authmapping
[admin:10-206-252-141]: > configure authmappingprofile authmapping
[admin:10-206-252-141]: authmappingprofile> mapping_rules index 2
New object being created
[admin:10-206-252-141]: authmappingprofile:mapping_rules> group_match
[admin:10-206-252-141]: authmappingprofile:mapping_rules:group_match> criteria auth_match_regex groups "sec-esp-(?P{tenant}\w*})-admin"
[admin:10-206-252-141]: authmappingprofile:mapping_rules:group_match> save
[admin:10-206-252-141]: authmappingprofile:mapping_rules> assign_tenant assign_matching_group_regex
[admin:10-206-252-141]: authmappingprofile:mapping_rules> assign_role assign_from_select_list
[admin:10-206-252-141]: authmappingprofile:mapping_rules> role_refs Tenant-Admin
[admin:10-206-252-141]: authmappingprofile:mapping_rules> default_tenant_ref admin
[admin:10-206-252-141]: authmappingprofile:mapping_rules> save
User Profile Mapping
With user profile mapping, it is possible to choose a user profile for remote users based on certain conditions.
To configure the user profile,
[admin:123]: systemconfiguration> admin_auth_configuration
[admin:123]: systemconfiguration:admin_auth_configuration> mapping_rules index 1
[admin:123]: systemconfiguration:admin_auth_configuration:mapping_rules> assign_userprofile assign_from_select_list
[admin:123]: systemconfiguration:admin_auth_configuration:mapping_rules> userprofile_ref Tacacs-Userprofile
[admin:123]: systemconfiguration:admin_auth_configuration:mapping_rules> save
Note: Ensure the user profile is already created. To know more about how to create and configure a user profile, click here.
View the user profile configuration as shown below:
[admin:123]: > show systemconfiguration
|----------------------------------|------------------------------------|
|Field | Value |
|----------------------------------|------------------------------------|
| Truncated Output |
| admin_auth_configuration | |
| auth_profile_ref | tacacs1 |
| mapping_rules[1] | |
| index | 1 |
| assign_tenant | ASSIGN_FROM_SELECT_LIST |
| tenant_attribute_name | |
| tenant_refs[1] | admin |
| assign_role | ASSIGN_FROM_SELECT_LIST |
| role_attribute_name | |
| role_refs[1] | Application-Admin |
| is_superuser | False |
| assign_userprofile | ASSIGN_FROM_SELECT_LIST |
| userprofile_ref | Tacacs-Userprofile |
| allow_local_user_login | True |
|----------------------------------|------------------------------------|
Notes:
- Alternate authentication profile is only supported when the primary authentication profile is SAML.
- Using SAML as the secondary authentication profile is not supported.
Avi will fallback to alternative auth configuration when primary auth is SAML and alternative auth is configured.
API/CLI will fallback to alternative auth configuration when the primary auth is SAML and an alternative auth is configured.
UI will also fall back to alternate auth if it is forced to local login even when the configured auth profile is SAML through https://<controller-ip>/#!/login?local=true.
Configuring Alternate Auth Profile
Alternate auth configuration is a part of admin_auth_configuration inside system_configuration and can be configured as explained below:
-
Login to the Avi shell.
-
Update the
admin_auth_configurationundersystemconfigurationas shown below:[admin:10-79-169-143]: systemconfiguration:admin_auth_configuration> where Tenant: admin Cloud: Default-Cloud +----------------------------------+-------------------------+ | Field | Value | +----------------------------------+-------------------------+ | auth_profile_ref | Avi01 SAML Configuration| | mapping_rules[1] | | | index | 0 | | assign_tenant | ASSIGN_FROM_SELECT_LIST | | tenant_refs[1] | admin | | assign_role | ASSIGN_FROM_SELECT_LIST | | role_refs[1] | Application-Admin | | is_superuser | False | | allow_local_user_login | True | | alternate_auth_configurations[1] | | | index | 1 | | auth_profile_ref | ldap-ad-user | | mapping_rules[1] | | | index | 1 | | assign_tenant | ASSIGN_FROM_SELECT_LIST | | tenant_refs[1] | admin | | assign_role | ASSIGN_FROM_SELECT_LIST | | role_refs[1] | Application-Admin | +----------------------------------+-------------------------+